Michael's Research in WS-Security Framework
 Amazon
In this project we focus on answering the question: Is the
WS-Security Framework adequate to handle every type of real-world scenario that
requires rigorous security?
Amazon
In this project we focus on answering the question: Is the
WS-Security Framework adequate to handle every type of real-world scenario that
requires rigorous security?
The scenario we are looking at is a loan bidding scenario.
The client logs on a loan bidding website and seeks bids for a loan of
certain size and certain period. The website sends the request out to the banks
it trusts and begins the negotiation process. Each bank has various departments
internally and each of them has certain responsibilities. In the event where a
loan cannot be fulfilled, a bank seeks bids from its 'partners' which
are independent entities who are not trusted by the loan bidding website. Of
course the details are much more complicated. This is just the general idea.
As you can see there are many security requirements that must be fulfilled by the WS-Security Framework in order for this scenario to migrate to web service.
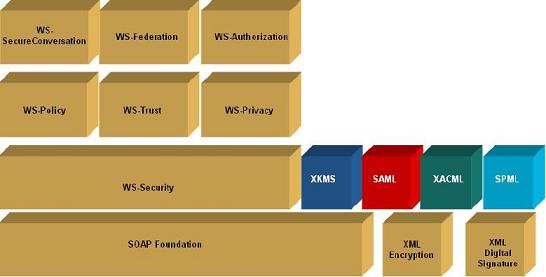
WS-Security is the foundation block that takes care of message-level security. Many extensions were drafted to handle different issues. They include WS-Trust, WS-Policy, WS-SecureConversation, WS-Federation, and so on.
We focused on WS-Security, WS-Trust, WS-Policy, and WS-SecureConversation to see if they could fulfill the security requirements of our scenario. Here is what WS-Framework looks like (from BEA Systems):

The conclusion is that the WS-Security Framework is adequate in most situations but there are things its specifications do not address and there are things we don't like about them. This project quickly evolves into a 30-page report detailing what we've found!
Although this project is not implementation-related, there are tons of specifications we need to read and UNDERSTAND. It's inevitably difficult to understand them because they are drafted by dozens of experienced engineers from industrial leaders like Microsoft, IBM, BEA, and Verisign.
Despite all that we managed to find several loopholes and potential scenarios that allow people to exploit those loopholes. Not bad for three weeks of work by only three people, right?